Can you trust the security of our vault?
Your competitors do.
We understand intellectual property. That’s why we’re committed to security and privacy across our platform — and why our customers trust us to help them find their next blockbuster products.


Security is at the heart of everything we do, across operations and processes. Our customers trust us with their most valuable and competitive assets. It’s an honor, and a responsibility we never forget.”
Justine Trubey
Chief Operating Officer
Operational Security
We’re committed to mitigating risk and ensuring that our services meet regulatory and security compliance requirements:
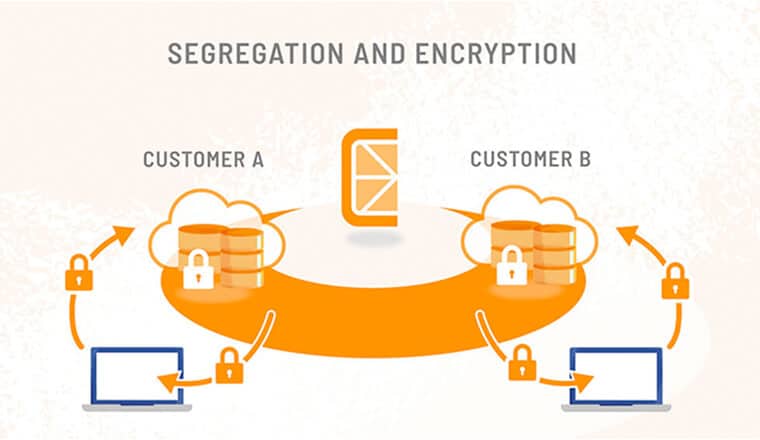
- Your data is classified, secured, and isolated while entrusted to Citrine
- Each customer’s production environment is hosted in a separate virtual private cloud
- Access to infrastructure, networks, and data is minimized with best-practice authentication systems.
Security and privacy by design
We designed the Citrine Platform with cybersecurity in mind:
- Change management processes
- Encryption in transit and at rest
- Account security
- Authorization security
- Cloud and network security
- Dedicated security team
- People security
- Continuous monitoring
Employee and third-party security
Our staff, contractors, and vendors must all comply with the same strict security and privacy requirements:
- Security awareness, phishing defense training, and mandatory background checks
- Citrine Assesses all potential and current vendors including: software supply chain suppliers, service providers and applications for compliance and competence.
- Amazon Web Services (AWS) data centers host all customer data and production systems
Driven by defense
We prepare for worst-case scenarios:
- Business continuity and disaster recovery planning
- Citrine Platform infrastructure is logged and continuously monitored by our engineering team
- Software code weakness and library code vulnerability assessments are built into our software development and deployment process.
FAQs
-
Who gets the Intellectual Property when AI for materials and chemicals is used?
Different companies have different business models. Citrine Informatics focuses on selling software and does not acquire any rights over the chemical and materials IP generated by customers using the platform. Read more in our blog.